Build relationships with vendors on multiple markets. When that market closes, users scramble to find alternatives. While WarpZone's 50,000+ listings provide excellent selection, smaller markets like Sklad offer superior security. These mistakes cost users money, compromise anonymity, or result in poor shopping experiences.
How To Access onion Sites Safely
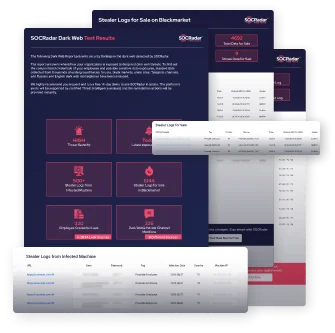
Specializing in data leaks, this forum has quickly gained traction and is now considered one of the top destinations for cybercriminals looking to buy or sell sensitive data. Despite the predominance of illicit activities, Dread also hosts conversations related to privacy and cybersecurity, reflecting the diverse range of topics covered on dark web forums. After the shutdown of RaidForums, BreachForums filled the gap by hosting discussions on exploits, data leaks, and cybercrime. Launched in March 2022 as a successor to RaidForums, BreachForums quickly became one of the leading forums for discussing data breaches and sharing stolen information. Despite its focus on illicit content, Nulled has a large and active user base.
2Easy admins opted to call the data packages for sale on this market “logs”. Threat actors buy and sell harvested data from browsers and devices. 2Easy is a quickly-growing dark web marketplace that’s based around a similar concept as the Genesis Market. InTheBox features over 400 custom “web injects” that threat actors can buy and use to hack into different mobile apps and services. Threat actors and aspiring cybercriminals have been flocking to Telegram channels and groups hoping to benefit from even better anonymity and default end-to-end encryption. It seems the older the market, the more likely these factors account for its closure.
- Established relationships with quality vendors provide reliability, while exploring new sellers discovers better options.
- And since these sites require access through Tor, they can't be reached over a normal connection.
- Haystak is a specialized dark web search engine with one of the largest indexes of .onion domains.
- What sets it apart is that it doesn’t track your searches or create user profiles, making it ideal for anonymous browsing.
- Use antivirus software to scan files and, if possible, open them in a secure, isolated environment.
- The market frequently makes headlines for releasing massive troves of stolen data, often as a way to advertise its services.
Finding Verified Market Links
In 2025, only a few markets stand out for their security, reliability, and vendor quality. With many dark web marketplaces coming and going, finding a safe and reputable platform is more important than ever. Silk Road was one of the first darknet markets, but in 2013, the FBI shut it down. Silk Road was once the most well-known dark web marketplace, but after its shutdown, many new markets took its place. The key differences between dark web markets and regular online stores are clear. Instead of using normal websites, these markets require special browsers like Tor that hide your location and identity.
- These sites often appear in onion directories, but they come with extreme risks.
- Launched in March 2022 as a successor to RaidForums, BreachForums quickly became one of the leading forums for discussing data breaches and sharing stolen information.
- The anonymity offered by Bitcoin and the Tor network provided a level of security for both buyers and sellers.
- However, the process is slower and more complex because of the encryption, anonymity protocols, and the unstructured nature of many dark websites.
- My focus lies in analyzing how these hidden networks shape online privacy, security, and digital ethics.
What Are Onion Sites?
By exclusively accepting Monero (XMR) for all transactions, the platform prioritizes anonymity and security for its users. The platform uses encryption and secure communication protocols to protect user data and maintain anonymity. The market is designed with a focus on user privacy, security, and a broad range of illicit goods and services.
What Is Typosquatting? Detection & Protection Guide
Due to its extensive inventory and reputation for reliability, Brian’s Club has maintained a significant presence on the dark web. It has built a reputation for being a reliable source of stolen credit card data and PII. What are initial access brokers IABs on the dark web? How can I tell if my personal data is on the dark web?
Phishing Attacks

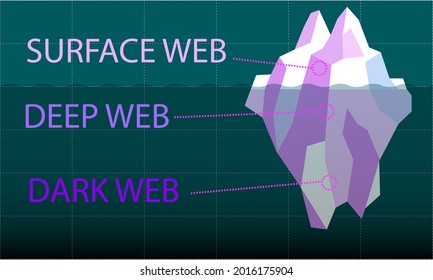
It relies on P2P connections and requires specialized tools and software. Lastly, the dark web is the portion of the deep web that is generally inaccessible and is much larger than the surface web. As a result, you cannot find them with a regular search engine.
Impact Of Law Enforcement And Policy Changes
Multiple vendors often sell identical products at different prices and quality levels. Quality vendors appreciate informed buyers and provide helpful responses. Before ordering, message vendors with specific questions about products, shipping times, or special requests. Professional vendors respond promptly to messages, answer questions clearly, and maintain courteous communication.
Advanced Security:
Mail2Tor is a more anonymous option, offering a simple inbox interface without storing logs or metadata. No marketplace should ever be trusted blindly, even if it looks professional. Users should be extremely cautious when exploring this category, as fake markets and scams are widespread. It allows anonymous users to ask and answer questions on controversial or privacy-sensitive topics. These engines are crucial for researchers and privacy advocates looking to explore the dark web beyond popular directories. Haystak offers a more advanced experience, including metadata previews and paid access to deep datasets.
Recent Darknet Market Updates

Using VPN before connecting to Tor provides additional anonymity layer. Comprehensive backup systems protect against data loss from hardware failures, attacks, or seizures. Decentralized infrastructure distributes market operations across multiple servers in different jurisdictions. Infrastructure security encompasses server hardening, DDoS protection, backup systems, and operational security practices. Lost recovery information means permanent account loss – a necessary trade-off for security. Account recovery mechanisms balance security with usability.

The Tor Browser encrypts your traffic, and will also allow you to access onion sites directly. There certainly are dark web markets, or other illegal platforms, in this space. Some onion links can be relatively long and random, but the nature of them makes it difficult to shut down a site, track user behaviors, or censor domains. Onion links are URLs that only end in ".onion" and can only be accessed from the Tor browser. As you use each tor link with trusted onion sites, you are one step closer to this vision where knowledge is uncensored, identity is protected, and exploration is limitless. Verified onion site lists help users navigate a living ecosystem that values authenticity and freedom over algorithmic control.
On the dark web, appearance can be deceiving, and often, it’s designed that way on purpose. Some are so well-built that they appear trustworthy until it’s too late. Many surface web results claiming to link to the “real” Hidden Wiki are actually trap sites.



