
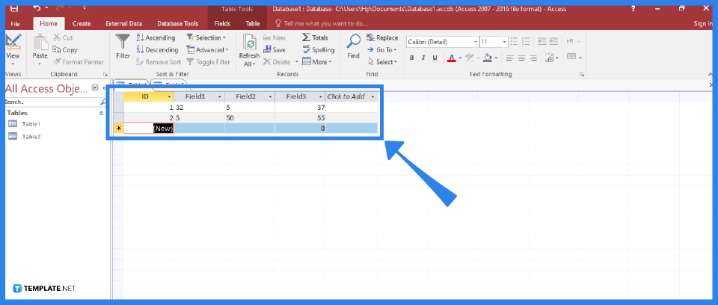
The evolution of darknet markets in 2025 demonstrates a clear maturation towards operational stability and transactional efficiency. Modern darknet markets feature streamlined interfaces that function similarly to their clearnet counterparts. The architecture of leading darknet markets in 2025 is fundamentally engineered to facilitate secure and efficient transactions. Buyers navigate these virtual marketplaces using search functions and category filters, from pharmaceuticals and digital goods to various other commodities, ensuring they find exactly what they require.
I recommend using a stick since DVDs have a read-only function after you’re done burning well and accessing the dark web required a bit of writing. It’s like in those movies where the doctors are experimenting on deadly viral strains from behind the safety of a glass enclosure. Because it’s easier to contain malware in a virtual environment, which can be fully controlled. If the signal goes through the Tor network first, your ISP will be able to see that you are attempting to connect to a Tor node.
The concept of darknets emerged as a response to concerns about digital privacy and government surveillance. Understanding darknets is essential for organizations to recognize and combat the threats they pose. Check for slight URL differences, poor website design, requests for unusual information, missing security features, and domain age. Use a VPN before connecting to Tor, disable JavaScript in Tor Browser, never download files, use Tails OS for maximum security, and never provide personal information. Avoid links from random forums, social media posts, or unverified sources. Legitimate links should match exactly with verified sources, have consistent uptime, and display proper SSL certificates.
Onion-Location is a HTTP header that web sites can use to advertise their onion counterpart. As such, it’s essential to know the risks of dark web access and how to protect yourself from them. People looking to access the dark web should be careful when downloading the Tor browser because it’s a prime target for hackers. Using Tor means your ISP won’t be able to see the sites you visit, but they will be able to see you accessed Tor. All you need to do is download and install Tor browser from the Play Store and connect to the Tor network. Aleksandar Kochovski is an expert in cybersecurity with a pronounced emphasis on secure cloud storage, a key component of modern cloud computing.
Archetyp What Are The Key Stages In Textile Production?
The “Hidden Wiki” (which can be accessed in a normal browser) offers a large collection of dark web links, but be careful, as many of those links are to dangerous websites. We’ve also previously mentioned the “dark users” that use the dark web for illegal reasons, but the less said about them, the better. ExpressVPN had created a .onion version of its website to allow greater privacy and anonymity for Tor browser users. The deep web contains sites and pages that are often prevented from being indexed by search engines and contain unlinked content.
- It is a wallet-based shop, meaning you must first deposit bitcoins into your wallet before purchasing any goods and services.
- Plus, Tor cannot protect against tracking at the entry and exit nodes of its network.
- For example, ProPublica—a renowned investigative journalism non-profit— uses the dark web to communicate with whistleblowers and ensure readers can access content without facing retaliation.
- We’ll cover it in a bit, but for now, let’s focus on ways users can access the black market.
- By leveraging automated dark web monitoring, organizations can mitigate risks, and take preventive measures before the leaked data is exploited.
Torrez Market
Darknets and dark markets present a multifaceted challenge to businesses and society as a whole. In repressive regimes, darknets play a vital role in enabling free speech and access to uncensored information. Darknets and dark markets have been at the center of numerous real-world use cases, often with negative consequences. These features help create a sense of ‘trust’ among users, even in the criminal ecosystem. The use of digital signatures can also help verify the authenticity of users and transactions.
On the same day, the FBI and Europol revealed they’d arrested 61 suspects and seized 50 darknet accounts worldwide. It specialized in narcotics, stolen data credit cards, credentials and contraband. On July 19 20, 2017 the Dutch and Europol publicly announced Hansa’s takedown, having collected data on 10,000 buyer addresses and seized 1,000 BTC in escrow.
How Does PGP Encryption Help On Darknet Markets?
Threat reports consistently rank it among the top ten darknet sites Top 10 Dark Web Markets. This survey highlights active and recently shuttered markets with actionable metrics and intelligence for threat hunters, CISOs, and red team leaders. Erika Rasure is globally-recognized as a leading consumer economics subject matter expert, researcher, and educator. Prioritize your safety, educate yourself on the laws governing your jurisdiction, and make responsible choices when using Darknet markets.

History Of Dark Web Marketplaces
The more specific you can be, the better, or else you’ll end up with the same search results you would find on Google. If you need academic journals, check out our article on using deep web search engines for academic and scholarly research. If you’re looking for a court case, for example, use your state or country’s public records search. These are okay, but specialized search engines are better than general ones for finding info on the deep web. Many of the best general deep web search engines, like Alltheweb, DeeperWeb, and CompletePlanet, have shut down or been acquired. Much of it is tucked away in databases that Google is either uninterested in or barred from crawling.
Types Of Dark Web Websites
It uses PGP encryption to protect sensitive data and messages, and accepts payments via Monera and Bitcoin to keep you anonymous on this marketplace. Bohemia is a modern dark web marketplace with a great user interface that is easy to use and navigate. However, the website has some security risks, and users experience glitches.
Communication Security And PGP Encryption
In October 2013, Project Black Flag closed and stole their users' bitcoins in the panic shortly after Silk Road's shut down. Atlantis, the first site to accept Litecoin as well as Bitcoin, closed in September 2013, just prior to the Silk Road raid, leaving users just one week to withdraw any coins. The months and years after Silk Road's closure were marked by a greatly increased number of shorter-lived markets as well as semi-regular law enforcement takedowns, hacks, scams and voluntary closures. The first marketplace to use both Tor and Bitcoin escrow was Silk Road, founded by Ross Ulbricht under pseudonym "Dread Pirate Roberts" in February 2011. They function primarily as black markets, selling or brokering transactions involving drugs, cyber-arms, weapons, counterfeit currency, stolen credit card details, forged documents, unlicensed pharmaceuticals, steroids, and other illicit goods as well as the sale of legal products. A darknet market is a commercial website on the dark web that operates via darknets such as Tor and I2P.
These digital currencies provide a degree of anonymity, as transactions are recorded on a public ledger but do not directly link users to their real-world identities. Transactions within dark markets predominantly involve cryptocurrencies like Bitcoin, Monero, or Ethereum. This means that the servers providing these services are only accessible via Tor and do not have a public IP address or domain name. The use of encrypted layers at each node creates a multi-layered “onion” of security, hence the name “The Onion Router.”
Centralized market escrow allows a market to close down and "exit" with the buyer's and vendor's cryptocurrency at any time. He recommends verifying market employees carefully, and to weed out law enforcement infiltration through barium meal tests. To protect against guard node deanonymization he recommends obfuscating traffic by investing in Tor relays which the market site will exclusively use.
The Dangers Of Darknet Marketplaces
- It’s very common for people to lose thousands of dollars on these markets.
- Such markets are typically accessible through the Tor network, which anonymizes traffic by routing it through multiple relays and encrypting each layer.
- Use this information responsibly and legally—for research, reporting, or educational purposes—not for participation.
- In fact, in most cases where people get caught doing something illicit using Tor, it’s because they’ve allowed themselves to be traced via other avenues.
- It has a bidding feature, with new batches of stolen data being frequently added.
- Tor is among the best private browsers for anonymous communications and internet freedom.
As a result, if you’ve used Mozilla, you’d be in familiar territory. This internet world has everything that the clearnet does. In simple words, imagine the Onion Network to be a whole internet world by itself. The clearnet is accessed using Google Chrome/Mozilla/Microsoft Edge/Safari and so on. The Clearnet is the normal internet that you or I surf everyday. It’s just as easy as accessing a social media or e-mail account that you’re familiar with.
Roundup – Best VPNs For The Dark Web
All this activity, this vision of a bustling marketplace, might make you think that navigating the dark web is easy. Only a tiny portion of the internet is accessible through a standard web browser—generally known as the “clear web”. Medical records, fee-based content, membership websites, and confidential corporate web pages are just a few examples of what makes up the deep web. Start by downloading the Tor browser, which is necessary to access dark web sites.



