While many sites offer valuable services, others may host illegal activities or harmful content. “.Onion” sites are specifically designed to keep traffic and data private, which means they’re blocked from being found by regular search engines. DuckDuckGo runs on the Tor network and lets you search any part of the internet without tracking or storing your data. Picture the regular internet as a bustling city, with easily accessible websites like stores or restaurants.
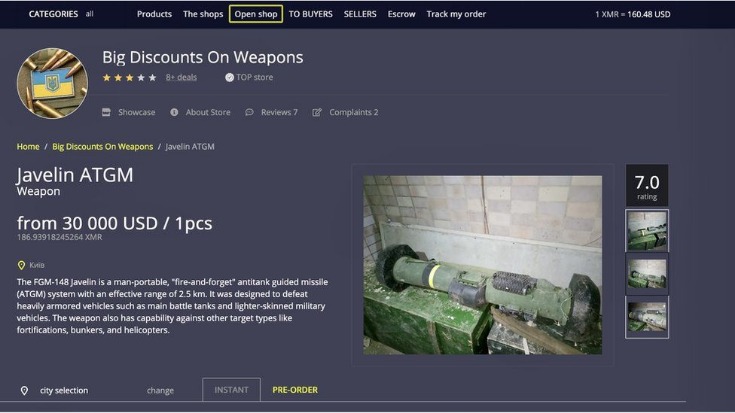
Though the dark web hosts illegal activities and malicious sites, it also serves legitimate purposes like secure communication for activists and journalists. Accessing the Dark Web, a part of the web that isn’t indexed by standard search engines, is not illegal in most countries. The dark web marketplaces thrive on the demand for illegal services and extreme content. Law enforcement agencies in many countries monitor the dark web to combat illegal activities.
- They moved to the dark web and started leaking the stolen user data.
- A VPN doesn’t encrypt traffic after it exits the Tor network.
- But even though it seems like there’s a lot out there, this only makes up about 4% of the entire internet.
- It can only be used to access hidden services specific to the I2P network.
- He has expertise in cyber threat intelligence, security analytics, security management and advanced threat protection.
- This is below the surface web and accounts for about 90% of all websites.
Don’t Download Files Or Click Ads
It is particularly vital for users in countries under oppressive regimes, offering a lifeline for free speech. The dark web might sound like a mysterious part of the internet, and in many ways, it is. This tactic can uncover plans for future attacks, identify key threat actors, or reveal supply chain compromises. Trained analysts may join forums or pose as buyers to access restricted conversations and inner circles.
Dark Web Tools And Services
Be aware, however, that there are sites for absolutely everything, from the benign to the very illegal. Take a look at the sites that these directories have collected and see what topics interest you. Do not explore random links to websites you aren't aware of or familiar with. Only visit trusted websites with URLs that are maintained by a trusted source. Tails enhances security, but Tor Browser with a VPN is sufficient for most privacy-conscious users.
How To Access The Dark Web Safely And Securely
No longer restricted to dial-up, many of us now consider access to a stable high-speed internet connection a critical element of our daily lives. Our editors thoroughly review and fact-check every article to ensure that our content meets the highest standards. Indeed, we follow strict guidelines that ensure our editorial content is never influenced by advertisers. We gather data from the best available sources, including vendor and retailer listings as well as other relevant and independent reviews sites. Websites on the dark web have .onion addresses, and they operate differently from regular sites.
What Is The Role Of Relays In Tor?
- For the dark web, though, you need an entirely different entry point known as an overlay network.
- A VPN will give you an extra layer of protection and anonymity, making it much safer to explore the dark web.
- This is the publicly accessible portion of the internet that can be indexed by search engines.
- Imperva DSF flexible architecture supports a wide range of data repositories and clouds, ensuring security controls and policies are applied consistently everywhere.
- Rather than weeding out the genuine web users from the criminals, many website owners find it easier just to block all Tor users.
So, when measuring the total network of live dark web sites alongside the surface web, only about 0.005% of the internet is the dark web. Researchers from Recorded Future estimated that while there are more than 55,000 existing onion domains, only 8,400 (or roughly 15%) of these sites were active. The dark web, by contrast, is configured on darknets — online networks that can be accessed only with special software and techniques.

Why Can’t You Use Google On The Dark Web?
During that period, on top of the risk of accidental disclosure and theft, governments and the police could ask ISPs to share data. These laws mark how long ISPs must save the data they collect. With all this data, your ISP could create a very accurate profile of you and link it to your IP address. It is highly advisable to take all the necessary security measures discussed in this article to protect yourself. You can access the dark web using your Android device by following a few steps.
Can Cybersecurity Teams Use The Dark Web To Track Threats?
No, simply accessing the dark web using Tor or other anonymizing browsers is not illegal. Safety concerns on the dark web include encountering criminal-run websites offering illegal goods and services, with the added risk of exploitation and theft. Although it is true that the dark web can be a hotspot for illegal activities due to its anonymity, it’s not just for those with nefarious intentions. It’s a segment of the internet hidden from view, not showing up in search results or accessible through regular web browsers. For this reason, many people prefer to use a VPN to encrypt their connection to the Tor network, thereby preventing their ISP from being able to detect that they are accessing the dark web.
What Are onion Domains?
Dark web websites don’t bear Internet Corporation for Assigned Names and Numbers (ICANN) domains, such as .com. This adds an extra layer of protection to thwart tracking and monitoring in case the traffic passes through a compromised exit node. A VPN encrypts your traffic before it goes into the Tor network. DuckDuckGo is the best dark web search engine, as it offers an excellent user experience akin to surface web search engines.
Disabling JavaScript, ActiveX, and Flash plugins, for example, will help to strengthen your privacy, though this may also cause some sites to run poorly. It has a range of settings you can configure to help with security and privacy. The easiest way to avoid falling victim to them is to simply not provide any personal data when browsing the dark web. There are a lot of these sites across the dark web, which is why you have to be extra careful. Often, these sites are made to look just like real, trusted platforms, such as banks, social media sites, or email providers.
NordVPN is our #1 recommendation for dark web browsing because of its security, privacy, and performance. Quality premium VPNs really do a great job at hiding your information and your IP address from onlookers who lurk on the internet. While it’s a lifeline for journalists and activists, it’s also crawling with scammers, digital pickpockets, and worse. Always remember, safety and legality come first when navigating this hidden part of the Internet.

Potential Risks And Threats On The Dark Web
Each of these options offers unique privacy features, with Whonix and Qubes for higher security setups, and Kodachi and Liberté for portability. Here’s a step-by-step guide to setting up Tails on a USB thumb drive and using it to access Tor. In this method, your traffic is routed through Tor before it reaches the VPN server, masking your IP address even from the VPN provider. However, keep in mind that the dark web is not organized like the regular internet. Whether you're a journalist, a privacy advocate, or just curious, this guide will walk you through how to access the dark web safely and responsibly.
A VPN’s ability to hide your Tor usage from your ISP and from government authorities makes for a valuable addition to your online privacy arsenal. Using a VPN in conjunction with the Tor Browser is an excellent way to keep your online travels secure and private. VPN Over Tor is when you first connect to the Tor network and then connect to your VPN.



